Threat modeling: our approach to identify digital vulnerabilities software solution

Securing information
Securing information is and will continue to be an important issue within Iquality. That is why we continue to invest in improving our services in that area. But what threats could there be? What would be the consequence if they became reality? And how do you actually know whether a software solution is sufficiently secure?
Securely developing digital solutions
In the media, you regularly hear about data breaches, denial-of-service (DDoS) attacks and ransomware. These are some of the potential threats that can be prevented by good information security. At Iquality, we pride ourselves on how we handle information security at every stage of the development process, but we also realize that we don't always have a clear picture of all possible threats. This is why we use a special method to detect threats.
Our approach
We analyze together with our customers in the design phase and when implementing major changes what concrete threats there may be. We look at the risk of the threats and the damage that could be caused. We look not only through "technical glasses", but emphatically also with an eye for the impact on all stakeholders.
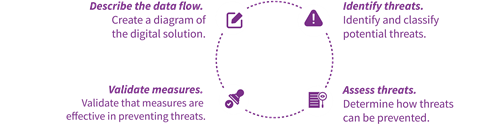
Threat Modeling
The method we use is called threat modeling. The knowledge of DevOps, (cloud) hosting, architecture, application development and domain knowledge of your organization itself is brought together in a joint session (usually 1 day). This involves a structured search for vulnerabilities in a system and how they can be exploited. The threats are then classified, how they can be prevented and a priority order is determined.
Engagement
Because you, the customer, are involved in the process yourself, you are immediately aware of the nature and severity of any risks that come to light. Iquality's UX-DEV-OPS team already knows your organization, which gives us a flying start.
Follow-up
The insights from the threat modeling session are used by the UX-DEV-OPS teams to make design adjustments or define tasks to eliminate vulnerabilities. Afterwards, it is validated whether the performed tasks actually removed the vulnerabilities. When you have a penetration test performed at a later stage, you can focus it directly on the weaknesses of a solution instead of asking a very broad question here to the pentester.
Secure your digital solution
When it comes to securing your software and systems, no method is as important as threat modeling. It is the key to identifying and mitigating threats before they can infiltrate systems. By applying threat modeling methodology, we are confident that your information is more secure. Do you need advice or want to spar on this topic? Let's get acquainted!


